One of the most important concepts administrators
need to understand when working with a directory service such as AD DS
is the division of responsibilities they face. A directory service is
very much like a web service. IT administrators of a web service are
responsible for the management of Microsoft Internet Information
Services (IIS) and the underlying operating system, not for the
maintenance of the content included in the websites the server will
host. Imagine having to change a comma here, a word there, a picture
here, or a phrase there in addition to having to perform all the other
work required to maintain a network environment. You would never have
time to do anything else but work!
In a web service, you must
divide responsibilities based on data and service management. IT is
responsible for service management, whereas the users are responsible
for data or content management. The same applies to the directory
service. AD DS is a distributed database that contains information about
the users, computers, servers, services, and more that run in your
network, hence its categorization as a network operating system (NOS) as
well as a Lightweight Directory Access Protocol (LDAP) directory
service. Because of this, administration activities are shared among
several members of your organization:
Users can update
their own records. If a user uses the Search Active Directory feature to
locate his or her own account record, he or she can change information
such as phone number, location, and so on.
Security
and distribution group managers, when assigned the role in AD DS, can
automatically manage group content if you assign this user right to
them. This is a good approach for reducing the workload system
administrators face when managing a NOS directory service. How would you
know whether a user should be a member of a group? In every case, when
you change group ownership, you respond to a request that was initiated
by someone else. Why not cut out the middle person and make group
managers directly responsible?
The help desk manages password resets. Each time a password must be reset, the help desk is involved.
System
administrators should focus most of their efforts on directory and DNS
service availability. After all, system administrators are there to
manage the availability of services and the data the directory contains,
not to manage the data itself.
When you plan your proactive
management strategy, focus on the service aspect of operations
management and delegate data management as much as possible. AD DS
delegation capabilities further enhance this model by allowing you to
assign object control to others in your organization discretely.
1. Twelve Categories of AD DS Administration
When you consider it,
Active Directory administration or management covers 12 major
activities. These activities and their breadth of coverage are described
in Table 1, which also outlines which tasks focus on data or content management and which are concentrated on service administration.
Table 1. AD DS Administration Activities
| TASK | DESCRIPTION | SERVICE | DATA |
|---|
| User and group account administration | This
includes user password resets, user creation and deactivation, user
group creation, and membership management. Should be delegated to the
help desk. | ☐ | ☑ |
| Endpoint device administration | All
computers in a Windows network environment must have a computer
account. This is how they interact with the directory and how the
directory interacts with them. Should be delegated to technicians. | ☐ | ☑ |
| Networked service administration | This
includes publication of network file shares, printers, Distributed File
System (DFS) shares, application directory partitions, and so on.
Should be delegated to the administrator of each service type. | ☑ | ☑ |
| Group Policy Object (GPO) management | GPOs
provide the most powerful model for object management in Windows Server
2008 R2. Should be delegated to appropriate technicians, but a central
GPO steward should control GPO proliferation. | ☑ | ☐ |
| DNS administration | DNS
is now tied closely to the directory, and the operation is based on a
properly functioning dynamic DNS service. Because DNS is integrated with
the directory, DNS administration is the responsibility of the domain
administrator. | ☑ | ☐ |
| Active Directory topology and replication management | Replication
is at the very core of the directory service operation. It covers the
configuration of subnets, sites, site links, site link bridges, and
bridgehead servers. You should rely heavily on the Knowledge Consistency
Checker (KCC)—a service that automatically generates replication
topologies based on the rules and guidelines you give it—to control
replication. This is the responsibility of the domain administrator. | ☑ | ☐ |
| Active Directory configuration management | Configuration administration involves forest, domain, and organizational unit (OU) design and implementation. It also involves Flexible
Single Master Operations (FSMO) roles, global catalog servers, and DCs,
including RODCs because these servers define the configuration of each
forest. One last activity that is related to configuration management is
time synchronization. AD
DS relies on the PDC Emulator role to synchronize time in the network.
These tasks are the responsibility of the forest and domain
administrators. | ☑ | ☐ |
| Active Directory schema management | AD
DS is a database, albeit a distributed one. As such, it includes a
database schema. Schema modifications are not done lightly because added
objects cannot normally be removed, although they can be deactivated,
renamed, and reused. This is the responsibility of the forest
administrator. | ☑ | ☐ |
| Information management | This
refers to the population of the directory with information about the
objects it contains. User objects, shared folders, and computer objects
can include owners; groups can include managers; printers and computers
can include location tracking information. The Active Directory Schema
Management console can be used to add or remove content from the global
catalog and determine whether an object should be indexed. You can also
assign NTDS quotas to make sure no one adds or extracts more information
than permitted in the directory. Delegate as many of the information
management tasks as possible. | ☐ | ☑ |
| Security administration | Security
administration covers everything from setting Domain Account policies
and assigning user rights to managing trusts and access control list
(ACL) and access control entry (ACE) administration. This is the
responsibility of the domain administrator or designated operators to
whom it has been delegated. | ☑ | ☐ |
| Database management | Database management involves Ntds.dit maintenance and AD DS object protection as well as GPO protection. Includes managing the LostandFound and LostandFoundConfig
containers, which are designed to collect homeless objects in your
directory. Also includes compacting the directory database on each DC.
Although AD DS regularly compacts its own database automatically, it is
good practice to compact it manually. This is the responsibility of the
domain administrator. | ☑ | ☐ |
| AD reporting | Generate
reports from your directory to know how it is structured, what it
contains, and how it runs. There is no default centralized reporting
tool, but you can export data at several levels of the directory. You
can also generate GPO reports with the Group Policy Management console.
This is the responsibility of the domain administrator and the GPO
steward. | ☑ | ☑ |
Depending on the size of your network, each of the activities included in Table 1
can be a job by itself. This is why you need to make sure you delegate
as much of the work as you can so that you can enlist as much help as
possible to ensure that the directory service is highly available at all
times. A couple of tools can help in particular situations.
1.1. Using Specops Gpupdate
When you work with
computer objects in the directory with Active Directory Users And
Computers, you can right-click the object and click Manage to launch the
Computer Management console with the computer as the focus for the
console, but this does not give you access to simpler functions such as
remote update of GPOs or the more common Start, Shut down, or Restart commands. However, you can obtain a simple and free add-on from Special Operations Software called Specops Gpupdate. Specops
Gpupdate is used here only as an example and is by no means an
endorsement. This tool automatically adds functionality to the Active
Directory Users And Computers console and gives you control over the
following activities:
Remotely updating GPOs on an object in the directory
Starting computers remotely, using Wake-on-LAN if enabled locally
Remotely restarting or shutting down the selected computer
Graphically reporting the results of an operation
In addition, Gpupdate allows
you to perform these tasks on single computer objects or on a collection
of objects by applying them to an entire OU. This is a good tool for
administrators who must manage computers and servers remotely.
Note:
OBTAINING SPECOPS GPUPDATE
To obtain Specops Gpupdate, go to http://www.specopssoft.com/products/specops-gpupdate. A one-time registration is required.
If you choose to implement
Specops Gpupdate, use the following procedure. You need local
administrator credentials if you are on a workstation or member server,
but you need domain administrator credentials on a DC. Also, you need to
be an Enterprise Administrator for the one-time Display Specifier
registration in the forest. This step is part of the prerequisite setups
for Specops Gpupdate. After the display specifiers have been added, you
can run the Setup.exe file on any computer on which you want to install
Specops Gpupdate.
Make sure the RSAT, especially the AD DS administration tools, are installed on your system.
Download the Specops Gpupdate tool from the Special Operations Software website and save it to the Documents folder on the system you want to install it to.
Run the self-extracting executable to extract the components to your Documents folder.
After the components are extracted, locate the setup.exe file. Double-click it to launch the setup.
On the welcome page, click the Start Installation link under Specops: GPUpdate.
Accept the license by clicking Accept.
Verify
that the prerequisites are installed. These include the .NET Framework,
PowerShell, and ADUC Menu Extensions. Add them if they are not
installed. Click Install when ready.
Click OK when the installation is complete.
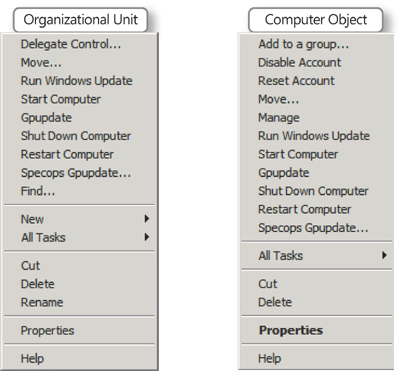
When you need to work with
computer objects, you can simply use the shortcut menu to access the new
administration features on either a computer object or an
organizational unit containing computer objects. (See Figure 1.) This tool is free and a good addition to any directory service.
1.2. Using AD DS Administration Tools
To perform the activities related to service administration in AD DS and DNS, you can use a series of tools.
You’ve already seen many of these tools as you read through the
previous lessons, but it is a good idea to review them here. Table 2
outlines which tools you can use for which task and where you can
locate them. In this table, the focus is on service, not data
administration. Many of these tools also work with Active Directory
Lightweight Directory Services (AD LDS) because it is based on the same
core code as AD DS.
Table 2. Common Service Administration Tools
| TOOL | DESCRIPTION | LOCATION |
|---|
| Active Directory Domains And Trusts | Administer trusts, domain and forest functional levels, and user principal name suffixes. | Administrative Tools program group |
| Active Directory Schema Snap-in | Modify
the schema for AD DS directories or AD LDS instances. You must use the
Regsvr32.exe command to register the Schmmgmt.dll first. | Custom MMC |
| Active Directory Sites And Services | Configure and manage replication scopes for AD DS directories and AD LDS instances. | Administrative Tools program group |
| Active Directory Users And Computers | Configure and manage the domain-centric FSMO roles as well as RODC features. | Administrative Tools program group |
| ADSI Edit | Query, view, and edit directory objects and attributes. | Administrative Tools program group |
| Best Practices Analyzer | Verify the configuration of a role as well as potential dependency errors. | Server Manager |
| CSVDE.exe | Import data into AD DS directories or AD LDS instances. | Command line |
| DCDiag.exe | Diagnose AD DS directories or AD LDS instances. | Command line |
| Dcpromo.exe | Add or remove the DC service. | Start menu, Search |
| DFSRadmin.exe | Manage
Distributed File System Replication, which is the system used when the
forest runs in Windows Server 2008 R2 functional level. | Command line |
| DNS Manager | Perform general maintenance of DNS servers. | Administration Tools program group or Server Manager |
| Dnscmd.exe | Manage all aspects of DNS servers. | Command line |
| DSACLS.exe | Control access control lists on directory objects. | Command line |
| Dsadd.exe | Add specific types of objects (users, groups, computers). | Command line |
| Dsamain.exe | Mount Active Directory store (.dit) backups or snapshots to identify their contents. | Command line |
| DSDButil.exe (installed with AD LDS and AD DS) | Perform maintenance of the AD DS store. Configure AD LDS ports. View AD LDS instances. | Command line |
| Dsget.exe | View the selected properties of a specific object (user, computer). | Command line |
| Dsmgmt.exe | Manage application partitions and operations master roles. | Command line |
| Dsmod.exe | Modify an existing object of a specific type (user, computer). | Command line |
| Dsmove.exe | Move an object to a new location within a directory. Also rename an existing object. | Command line |
| Dsquery.exe | Query the directory for a specific object type according to specified criteria. | Command line |
| Dsrm.exe | Delete an object of a specific type or a collection of objects. | Command line |
| Event Viewer | Audit AD DS or AD LDS changes and log old and new values for both objects and attributes. | Administrative Tools program group |
| GPfixup.exe | Repair domain name dependencies in Group Policy objects. Also, relink Group Policy objects after a domain rename operation. | Command line |
| Group Policy Management Console | Create, manage, back up, and restore GPOs. | Administrative Tools program group |
| Ipconfig | Display and modify IP configuration details. | Command line |
| Ksetup.exe | Configure a client to use a Kerberos v5 realm instead of an AD DS domain. | Command line |
| Ktpass.exe | Configure a non-Windows Kerberos service as a security principal in AD DS. | Command line |
| LDIFDE.exe | Import data into AD LDS instances. | Command line |
| Ldp.exe | Perform LDAP operations against the directory. | Start menu, Search |
| Movetree.exe | Move objects between domains in a forest. | Download from Microsoft.com |
| Netdom.exe | Manage computer accounts, domains, and trust relationships. | Command line |
| Nltest.exe | Query replication status or verify trust relationships. | Command line |
| Nslookup.exe | View information on name servers to diagnose DNS infrastructure problems. | Command line |
| Ntdsutil.exe (installed with AD DS, not AD LDS) | Perform database maintenance on the AD DS store. | Command line |
| Repadmin.exe | Diagnose Active Directory replication problems between domain controllers running Microsoft Windows operating systems. | Command line |
| Server Manager | Manage existing AD DS domains or AD LDS instances. | Administrative Tools program group |
| System Monitor | Create charts and graphs of server performance trends. Determine performance benchmarks. | Server Manager, Diagnostics, Reliability, and Performance |
| Ultrasound (Ultrasound.exe) | Troubleshoot and diagnose replication between DCs that use FRS. Relies on Windows Management Instrumentation (WMI). | Download from Microsoft.com |
| W32tm.exe | View settings, manage configuration, or diagnose problems with Windows Time. | Command line |
| Windows PowerShell | Interact with and automate AD DS operations. | Administrative Tools program group |
| Windows Server Backup | Back up or restore AD DS directories or AD LDS instances and their contents. | Administrative Tools program group |
Note:
MORE INFO FINDING AND DOWNLOADING TOOLS
To locate the Movetree.exe command, go to http://www.microsoft.com/downloads/details.aspx?FamilyID=96a35011-fd83-419d-939b-9a772ea2df90&DisplayLang=en.
Obtain the .cab file and extract all files named movetree.* from the
file. Note that not all tools contained within this file work with
Windows Server 2008 R2; Windows Server 2003 support tools are not
supported on Windows Server 2008 R2. For example, the ReplMon.exe tool simply will not launch.
To obtain Ultrasound, go to http://www.microsoft.com/Downloads/details.aspx?FamilyID=61acb9b9-c354-4f98-a823-24cc0da73b50&displaylang=en.
2. Performing Offline Maintenance
One significant change in
AD DS from previous versions is the transformation of the DC role into a
controllable service. In previous versions of Windows Server, the DC
role was monolithic: to stop the service, you needed to stop the DC as a
whole. This meant that when you needed to perform maintenance on the
Ntds.dit database—the database that contains the directory store—you had
to shut down a DC and restart it in Directory
Services Repair Mode. Because of this, there was no way to automate the
database maintenance operations. Consequently, most domain
administrators never performed any database maintenance at all.
Performing no maintenance is not a valid approach to systems management.
Every database works the same
way: As new records are added, the database allocates additional space
to store information associated with the record. However, when the
record is deleted, the allocated space is not recovered. You need to
perform database compaction activities to recover this space. The AD DS
service does perform some automatic database compaction, but this
compaction does not recover lost space within the database; it only
rearranges data to make it easier to access. To recover lost space, you
must take the database offline and run a compaction and defragmentation sequence against it.
However, with AD DS and Windows
Server 2008 R2, the AD DS service is now a manageable service that can
be started and stopped like all Windows Server services. This means that
to perform database maintenance activities, you no longer need to shut
down the DC to restart it in Directory Services Repair Mode. It also
means that because the service behaves natively, you can script the
defragmentation and compaction operations through basic command-line
tools.
Note that to stop the AD DS
service, the DC must be able to communicate with another DC that is
running the service. If it cannot, you will not be able to stop the
service. AD DS includes automatic checks and verifications that ensure
that at least one DC is available at all times; otherwise, no one will
be able to log on to the network.